WannaCry Ransomware Analysis
WannaCry ransomware has been the most widespread ransomware. A ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid.
It is worth noting that the first WannaCry infection was reported on February 10th then again on the 25th. We will refer to this as “version 1.” This did not have a widespread impact.
On the afternoon of Friday, May 12th 2017, what we will refer to as “version 2” of WannaCry started to infect systems around the world. WannaCry quickly spread to affect organizations such as the UK’s NHS. An example of the ransom demand can be seen below: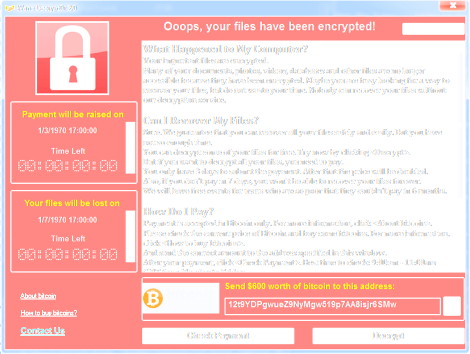
Figure 1: Example of WannaCry Ransomware Demand
By around 4:00 PM on Friday, there were reportedly around 36,000 detections, which were spreading globally. There had been some conjecture on social media that a PDF was the cause of the infection, but this was found to be benign. Currently, there is speculation that the initial vector of the attack was through a phishing email. While this is a likely cause, this has not yet been confirmed, and it may take some time before the root of the infection comes to light.
After numerous malware analysts around the world started to dissect WannaCry, it quickly came to light that WannaCry makes use of “EternalBlue”, the exploit, and “DoublePulsar,” the backdoor/implant. The relevance of this finding is key, because back on the April 14th, a hacking group called “Shadow Brokers” leaked a series of files that they claimed were stolen from the NSA.
EternalBlue essentially is the exploit found in WannaCry that takes advantage of exploiting a core Windows networking protocol called Server Message Block (SMB). As SMB is so intertwined with numerous versions of Windows, this exploit can affect Windows XP up through Windows Server 2016.
For reference, this vulnerability was addressed in Common Vulnerabilities and Exposures (CVE) ids CVE-2017-143 through 148. Microsoft did, in fact, release a patch for this vulnerability on March 14th (in Security Bulletin MS17-010); however, companies that did not apply this patch have been vulnerable ever since. Despite Windows XP being already past end–of-life, Microsoft issued an emergency patch to address this vulnerability on Friday night. This was done as a good-will deed in order to help customers who are still running Windows XP to avoid the spread of WannaCry.
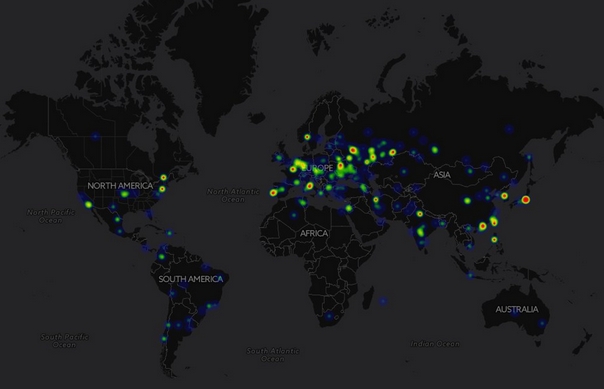
By Friday night, the National Crime Agency, Interpol, and numerous other organizations around the world had issued statements to notify and warn businesses in their corresponding countries of the wide-scale attack. Below is a map of infections that had occurred between Saturday (May 13th) and Sunday (May 14th). By that time, around 60,000 computers in 74 countries were infected. Companies in many industries were affected including: global shipping, auto manufacturers, health care, and educational institutions.
Figure 2: A Map of WannaCry Infections as of Sunday, May 14th (via @malrhunterteam)
By Saturday afternoon, Edward Snowden had commented on the drama underway. Snowden made a clear statement about NSA involvement in the attack: “Despite warnings, @NSAGov built dangerous attack tools that could target Western software. Today we see the cost.”
By Sunday evening, the BBC had reported that there are now more than 200,000 computers infected in over 150 countries, according to Europol. Microsoft later blamed WannaCry on “NSA Vulnerability Hoarding Program.”
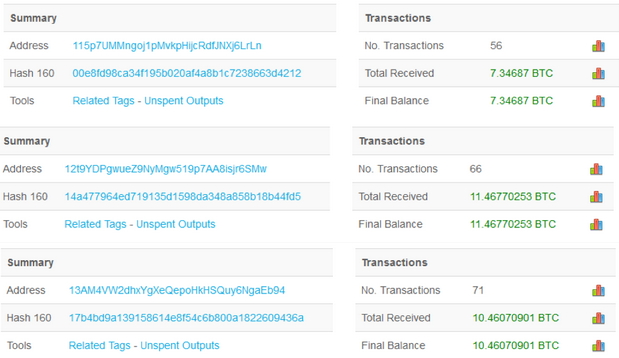
As of Monday morning, BlockChain reports the following statistics showing how many transactions and the resulting BitCoin balance for each of the three BitCoin addresses supplied within the malicious file. This translates to approximately $51,290 in revenue for attackers.
Figure 3. Bitcoin Payments for WannaCry Ransom (via https://blockchain.info)
High-Level Technical Overview
When the malicious file is run, a number of things happen. First, a call is made to a host. If the connection is successful, the program exits. (Refer to the “Kill Switch” section further down for more.) A Windows service called the “Windows Security Center Service” is created, and shadow copies (which are a snapshot/backup technology built into Windows) are then deleted.
The malicious file then extracts numerous other files, which include multi-lingual files containing the ransom note in 28 different languages, a background display image which gets set as the background/wallpaper for the infected system (shown below), and several other files which play a part in the encryption, communication and decryption stages.Figure 4. Background Image Used for Infected Systems
There are notably three unique Bitcoin addresses, which are used to collect the ransom funds. The communication is first setup using Tor, which is a known program that helps achieve anonymity online.
Files are then modified and all users are given full access rights, and then encrypted. Each file name is appended with the extension WNCRY. For example, if you have a Word document saved as “finance.docx,” this would then be renamed and encrypted to become “finance.docx.wncry.”
As WannaCry uses Microsoft Enhanced RSA and AES cryptography, what this essentially means is that only after the ransom is paid (which is between $300 and $600), the files will then become decrypted and readable once more. Despite reclaiming files, the integrity of the system by this time would be severely impacted—the user or company would still be looking to restore from backup, until such time that a decryption tool is released.
The Kill Switch
A researcher known as “MalwareTech” on Twitter discovered that the domain name that WannaCry tries to first connect to was unregistered. After researching further, he decided to register the domain name. This had a fast-acting impact, because doing so essentially stopped WannaCry from running any subsequent steps. The only caveat of the kill switch is that infected systems that connect through a proxy server out to the Internet are, in fact, still vulnerable.
Advice for Defending Against WannaCry
Due to the widespread impact and scale of this attack, it is advised that anyone running Windows XP through to Server 2012, apply the MS17-010 emergency patch issued on Friday.
For Windows environments that are still utilizing the SMB networking protocol, it is strongly advised that you consider whether it is viable to disable SMB version 1 at the earliest opportunity. Caution should be taken as there may be legacy applications in the environment that depend on SMBv1.
In addition, it is recommended that any hosts that are externally accessible over SMB have inbound traffic for ports 139 and 445 blocked, even at the host firewall level.
– LogRhythm
Students or Professionals engaged in cyber security, can use the below links to be updated on Security related issues