Learning Resources
Electronic mail, also known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the same time, in common with instant messaging. Today's email systems are based on a store-and-forward model. Email servers accept, forward, deliver and store messages. Neither the users nor their computers are required to be online simultaneously; they need connect only briefly, typically to an email server, for as long as it takes to send or receive messages.
Short for electronic mail, the transmission of messages over communications networks. The messages can be notes entered from the keyboard or electronic files stored on disk. Most mainframes, minicomputers, and computer networks have an e-mail system. Some electronic-mail systems are confined to a single computer system or network, but others have gateways to other computer systems, enabling users to send electronic mail anywhere in the world. Companies that are fully computerized make extensive use of e-mail because it is fast, flexible, and reliable.
Sent messages are stored in electronic mailboxes until the recipient fetches them. To see if you have any mail, you may have to check your electronic mailbox periodically, although many systems alert you when mail is received. After reading your mail, you can store it in a text file, forward it to other users, or delete it. Copies of memos can be printed out on a printer if you want a paper copy.
All online services and Internet Service Providers (ISPs) offer e-mail, and most also support gateways so that you can exchange mail with users of other systems. Usually, it takes only a few seconds or minutes for mail to arrive at its destination. This is a particularly effective way to communicate with a group because you can broadcast a message or document to everyone in the group at once.
An pictorial representation of e-mail.

Symbol used in e-mail -
.svg/120px-(at).svg.png)
Advantages and Limitations of Email
Advantages
Email has a number of advantages over some other forms of communication. It's quick, convenient, and non intrusive.
- You can communicate quickly with anyone on the Internet. Email usually reaches its destination in a matter of minutes or seconds.
- The cost of communication has nothing to do with distance, and in many cases, the cost doesn't depend on the size of the message. The cost is based on the number of messages, not where they're sent.
- You can send letters, notes, files, data, or reports all using the same techniques. Once you learn how to use your email program, everything is sent the same way.
- You don't have to worry about interrupting someone when you send email. The email is sent and delivered by one computer system communicating with the Internet. Although it is put into someone's mailbox, the recipient isn't interrupted by the arrival of email.
- You can deal with your email at a convenient time. You don't have to be interrupted when email arrives, and you can read it or work with it when you have the time. Also, you can send it at a convenient time. It doesn't have to be written or sent at a time when you know the recipient will be available.
- You don't have to play phone tag or make an appointment to communicate with someone. Once again, the email is sent when it's convenient for you, and it can arrive even when the recipient isn't using her computer.
- You don't have to be shy about using email to communicate with anyone. Email isn't anonymous-each message carries the return address of the sender-but you can write to anyone with an Internet address. All the messages appear the same to the person who gets the email. The messages are generally judged on what's in them, not where they're from.
Limitations
- Email isn't necessarily private. Since messages are passed from one system to another, and sometimes through several systems or networks, there are many opportunities for someone to intercept or read email. Many types of computer systems have protections built in to stop users from reading others' email, but it's still possible for a system administrator to read the email on a system or for someone to bypass the security of a computer system. This is discussed in more detail in Chapter 9.
- It's difficult to express emotion using email. The recipient doesn't have the benefit of seeing your facial expressions or hearing your voice. You have to be careful with humor or sarcasm, since it's easy for someone to take your message the wrong way and interpret your words in a manner different from how you mean them.
- You can receive too much email, and you have to take the time to deal with it. You'll probably have some limit on the amount of space your email can take up on the computer system you use. If you join a discussion group (as described later in this chapter), it's possible that you'll be flooded with messages that may be of little value or even offensive, since you can receive "junk" email in the same way you receive other types of junk mail. Some people see email as an inexpensive way to market products or advertise. In any of these cases, you may have to take active steps to delete the email you receive and try to stop it from being sent to you in the first place.
- It's possible to forge email. This is not common, but it is possible to forge the address of the sender. You may want to take steps to confirm the source of some email you receive.
- Some email systems can send or receive text files only. Even though you can send and receive images, programs, files produced by word processing programs, or multimedia messages, some folks may not be able to properly view your message.
Although there are some drawbacks to using email, it's still an effective and popular way to communicate.
To send an email message to someone you must know his/her email address. An email address is made up of three parts. The user's ID (or username), which comes before an @ sign, the @ sign itself, and the name of the computer where the user receives email. Each computer connected to the Internet has its own unique address. Because of these unique addresses, email can be delivered clear across the world through the Internet, much the same way that giving your street address, town, and postal code allows physical mail to be delivered to you. An example of an email address is:
johndoe@some.computer.edu
Every character is important, though upper and lower case do not matter. The ID is to the left of the @ sign. It is often a shortened version of the persons' name, such as their first initial and last name or their first name and last initial. However, many people are allowed to choose their IDs and use nicknames. In some cases the ID may be generated automatically by the computer and thus be a set of letters and numbers such as ab123. The person's home computer address is to the right of the @ sign and usually has some connection to the site where the user has his/her email account. This computer name is often called the "host" or "domain" name. For instance, a student at State University may have a machine name like state.edu. Users of the America On-Line service have addresses ending in aol.com.
There are some common endings on Internet host names. They include the ones listed below.
.edu -- usually higher education, but sometimes K-12
.gov -- Government entity
.com -- commercial organization
.org -- organization - usually non-profit
.mil -- Military
An e-mail message has always been nothing more than a simple text message -- a piece of text sent to a recipient. In the beginning and even today, e-mail messages tend to be short pieces of text, although the ability to add attachments now makes many messages quite long. Even with attachments, however, e-mail messages continue to be text messages -- we'll see why when we get to the section on attachments.
E-mail Clients
You've probably already received several e-mail messages today. To look at them, you use some sort of e-mail client. Many people use well-known, stand-alone clients like Microsoft Outlook, Outlook Express, Eudora or Pegasus. People who subscribe to free e-mail services like Hotmail or Yahoo use an e-mail client that appears in a Web page. If you're an AOL customer, you use AOL's e-mail reader. No matter which type of client you're using, it generally does four things:
- Shows you a list of all of the messages in your mailbox by displaying the message headers. The header shows you who sent the mail, the subject of the mail and may also show the time and date of the message and the message size.
- Lets you select a message header and read the body of the e-mail message.
- Let's you create new messages and send them. You type in the e-mail address of the recipient and the subject for the message, and then type the body of the message.
- Lets you add attachments to messages you send and save the attachments from messages you receive.
Sophisticated e-mail clients may have all sorts of bells and whistles, but at the core, this is all that an e-mail client does.
E-mail Operations
The diagram shows a typical sequence of events that takes place when Alice composes a message using her mail user agent (MUA). She enters the email address of her correspondent, and hits the "send" button. How email works
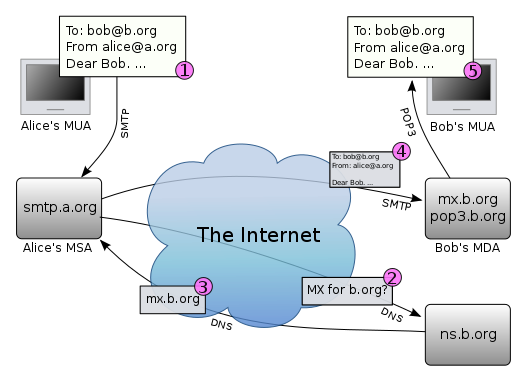
- Her MUA formats the message in email format and uses the Submission Protocol (a profile of the Simple Mail Transfer Protocol (SMTP), see RFC 6409) to send the message to the local mail submission agent (MSA), in this case smtp.a.org, run by Alice's internet service provider (ISP).
- The MSA looks at the destination address provided in the SMTP protocol (not from the message header), in this case bob@b.org. An Internet email address is a string of the form localpart@exampledomain. The part before the @ sign is the local part of the address, often the username of the recipient, and the part after the @ sign is a domain name or a fully qualified domain name. The MSA resolves a domain name to determine the fully qualified domain name of the mail exchange server in the Domain Name System (DNS).
- The DNS server for the b.org domain, ns.b.org, responds with any MX records listing the mail exchange servers for that domain, in this case mx.b.org, a message transfer agent (MTA) server run by Bob's ISP.
-
smtp.a.org sends the message to mx.b.org using SMTP.

