Cyber crime is an ever increasing threat to the security of computer systems. Break-in methods are becoming more and more sophisticated and complicated. This necessitates the use of complex security systems and makes it difficult – sometimes almost impossible – to catch offenders. This makes it necessary to search for new methods of hunting offenders, going beyond information technology methods. Psychological profiling can be applied to the field of cyber crimes.
Psychological profiling is currently mainly used in murder cases. In the case of computer crimes, psychological knowledge and experience can also certainly be applied. Such experience and knowledge allow us to interpret pieces of evidence collected at the scene in such a way as to enable us to determine the offender’s personality type. This is based on the fact that according to basic rules of profiling there is a relation between an offender’s personality and an act s/he committed. As a result, based on the method of operating ( modus operandi) and traces left, one can infer about the psychophysical characteristics of an offender, including an offender’s motivation and behaviour in the broadest sense. Identical relations concern network attacks. Perpetrators of computer crimes count on the anonymity of the internet, but this anonymity does not concern their modus operandi , motivation and “signatures” they leave. According to McQuade, each cyber criminal has his/her own techniques and software which s/he uses for break-ins. computer crimes are often of a serial nature, so it is possible to determine an offender’s profile. Erbschloe postulates the necessity of preparing profiles of perpetrators of internet terrorist attacks, considering them as an increasing threat to network security.
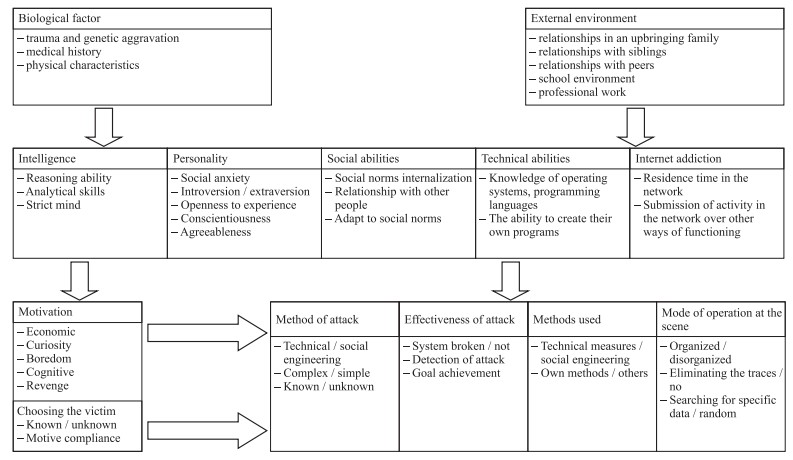
To explain an individual’s functioning, it is necessary to refer to a construct encompassing not just a selected range of human functioning, but a holistic concept (of human functioning). An example of such an understanding of an individual is the five-factor definition of personality in the FFT model (Five Factor Theory) by costa and Mc crae.
It encompasses a number of aspects connected with personality and factors that are dependent on it, which is why it seems to be reasonable to apply it to the concept of psychological profiling, as a global view of an offender. According to the authors of this concept, five personality traits are central elements, defined as basic tendencies: neuroticism, extroversion, openness, agreeableness and conscientiousness. Biological bases (traits), understood here as genetically determined individual characteristics, have an influence on the level of these factors. characteristic adaptations, according to the authors, constitute another element, dependent on basic tendencies and external influences and thus culturally determined phenomena, personal aspirations and attitudes. An important element of this model is the assumption that despite the fact that this theory concentrates on personality characteristics, the following are also included among basic tendencies: cognitive skills, artistic talents, sexual orientation and “all the psychological machinery lying at the basis of learning, perception and other psychological functions”. This means that this model can be included among holistic conceptions of human personality, encompassing the influence of both biological and social factors in its development.
Two groups of factors have an influence on central elements
- Biological factors, namely a set of characteristics (properties) which take into account the physical traits of an individual, as well as injuries and genetic burdens, and past diseases. Previous results of research indicate their influence on the development of intelligence and personality. There are also reports in the literature about dyslexia, dyscalculia, and even Asperger’s syndrome occurring among hackers.
- The external environment, encompassing widely understood environmental influences, and thus family influence, the upbringing and education process, relations with peers and siblings, as well as later functioning at school and at work. There are reports in the literature on bad relationships with parents and often divorces in hackers’ families of origin. Other researchers also write about difficulties at school, playing truant or abuse of psycho-active substances. The author of the present work assumes that the external environment influences the development of intelligence, personality, social skills, technical skills and degree of addiction to the internet.
Studies by costa and McRae in five cultures confirm this assumption. Five factors of equal importance make up the central elements:
- Intelligence – understood here as ability to reason, analyse and think logically, which are an important element in the effectiveness of an attack. In the case of hackers’ attacks, at least an average IQ is necessary, but it is also possible to break-in using such tools as special programs downloaded from the network. The latter type of operation does not require a high intelligence quotient.
- Personality – understood as a set of characteristics which are crucial for effectiveness of attacks. It should be emphasised that unlike costa and McRae, the author understands it as an element that is equally important to other factors, but not the most important for a hacker’s activities. Understanding these factors according to the earlier mentioned FFT theory, one may suppose that in the structure of this set of characteristics, of particular significance is the extroversion/introversion dimension, which determines the method of attack (use of technical methods or social influence techniques in the case of obtaining necessary information directly from a user). One may also hypothesise that a high level of neuroticism and openness to new experiences will be linked to strong motivation to act and aspiration to break the system. A high level of neuroticism may condition abuse of communication via the network, and also a strong need to maintain one’s anonymity. One may suppose that openness to experiences determines being “up-to-date” – a need to learn new systems, as well as creativity and unconventionality in breaking security measures. In turn, one may assume that agreeableness and conscientiousness condition effectiveness at work and in fulfilling one’s duties. According to the literature, both spheres are often neglected by hackers. These characteristics are well illustrated by Shaw’s studies. As transpires from his studies, insiders (employees breaking into servers at their own place of work) have a tendency to break the rules being in force at their place of work, ignoring superiors and coming into conflicts with them.
- Social skills – they constitute a dimension which determines the individual’s functioning in a group, internalisation of social norms and using them in private and professional life, and thus in broadly defined social adaptation. Social skills remain in relation to intelligence and technical skills. The literature emphasises the fact of low social skills among hackers, consisting in difficulties in relations with family and colleagues, sense of alienation and inability to form close interpersonal relations.
- Technical skills – this element should be understood as general knowledge concerning programming languages, computer systems, network functioning (with special emphasis on network security), and also knowledge about other groups of applications used, among other things, for data base development. Information technology specialists draw attention to the necessity of knowing at least several programming languages ( c, c++ and PeRL are most frequently mentioned here). According to Schell and Dodge, hackers should also know the principles of sending data through the network and at least two operating systems, one of which should be based on UNIX. knowledge in this area is crucial, because it allows them to make use of weaknesses of a system when breaking in.
- Addiction to the internet – this element seems to be related to the effectiveness of an attack, but its presence is not necessary in all cases. Time devoted to computers may translate into skills in using them. The literature here talks about at least 50 hours per week spent after work on the internet. There are a number of internal relations between central elements. The psychological literature indicates correlations between intelligence and personality. Intelligence also influences social and technical skills. There is a relation between personality and social skills that are related to abuse of the internet. Social skills, apart from relations mentioned earlier, influence technical skills and addiction to the internet. Here there is also a relation between technical skills and abuse of the internet, but it does not manifest in all cases.