Social engineering is the act of obtaining or attempting to obtain otherwise secure data by conning an individual into revealing secure information. It is successful because its victims innately want to trust other people and are naturally helpful. The victims of social engineering are tricked into releasing information that they do not realize will be used to attack a computer network. For example, an employee in an enterprise may be tricked into revealing an employee identification number to someone who is pretending to be someone he trusts or representing someone he trusts. While that employee number may not seem valuable to the employee, which makes it easier for him to reveal the information in the first place, the social engineer can use that employee number in conjunction with other information that has been gathered to get closer to finding a way into the enterprise network.
The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious software–that will give them access to your passwords and bank information as well as giving them control over your computer.
Criminals use social engineering tactics because it is usually easier to exploit natural inclination to trust than it is to discover ways to hack your software. For example, it is much easier to fool someone into giving you their password than it is for you to try hacking their password (unless the password is really weak).
Security is all about knowing who and what to trust. Knowing when, and when not to, to take a person at their word; when to trust that the person you are communicating with is indeed the person you think you are communicating with; when to trust that a website is or isn’t legitimate; when to trust that the person on the phone is or isn’t legitimate; when providing your information is or isn’t a good idea.
It doesn’t matter how many locks and deadbolts are on your doors and windows, or if have guard dogs, alarm systems, floodlights, fences with barbed wire, and armed security personnel; if you trust the person at the gate who says he is the pizza delivery guy and you let him in without first checking to see if he is legitimate you are completely exposed to whatever risk he represents.
Social engineering attacks typically originate from one of three zones i.e. internal, trusted and external.
- Internal threats come from employees who manipulate other employees to gather sensitive information and access to IT systems. These offenders can include disgruntled employees, temporary employees, employees with criminal tendencies, and ancillary workers such as housekeeping and maintenance staff. Enterprises grant a certain amount of trust to all of these individuals, which can make it easier for them to execute attacks.
- Trusted threats come from other individuals who are formally associated with your organization on a regular basis but are not on your payroll. These can include contractors and consultants, as well as partner organizations. Often, these individuals have a very high level of trust, and thus have access to sensitive data and systems. Yet such potential risks are rarely incorporated into security plans.
- External threats come from people who are not associated with your organization. This category can include recreational hackers, competitors wanting to uncover confidential information, or criminals wanting to steal something. These people have no established trust with your organization, so they look to create short-term trust by using various social engineering techniques.
Some examples of these techniques are:
- Playing the role of an authority, such as an IT administrator.
- Playing the role of an end user.
- Playing the role of someone from a partner organization.
- Playing the role of a telecom technician or another individual who would have physical access to the company’s data systems.
- Tricking an employee into planting malicious software on internal systems.
- Stealing the identity of someone with inside access to IT systems.
Individuals who use social engineering techniques usually follow a common pattern of activity that called the Social Engineering Attack Cycle, which is
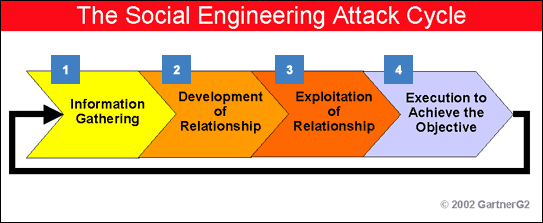
In the first phase, information gathering, an attacker uses various techniques to track down detailed information that can be used to gain the trust of an individual connected to the targeted organization. The attacker will then use this information to develop a relationship with the individual in phase 2 of the attack cycle. This can take one phone call or it can happen over a period of weeks or even months.
After the relationship is established, the attacker will exploit the relationship (phase 3) to get the target to reveal information or perform an action that would not otherwise take place. Phase 3 either accomplishes the attacker’s objective or opens the door to achieving the final objective in phase 4.

