Identity management is the set of business processes, and a supporting infrastructure for the creation, maintenance, and use of digital identities. Identity Management also called as identity and Access Management (or IAM).
Managing identities and access control for cloud computing applications remains one of the greatest challenges. Identity management (IDM) also assumes a significant part of cloud security. Cloud deployments are dynamic with servers, IP addresses and services started or decommissioned or re-started thus, needing dynamic governance of typical IDM issues like, provisioning/de-provisioning, synchronization, entitlement, lifecycle management, etc.
Main components
- Directory Services repositories for storing and managing accounts, identity information, and security credentials.
- Access Management the process of authenticating credentials and controlling access to networked resources based on trust and identity.
- Identity Life Cycle Management the processes used to create and delete accounts, manage account and entitlement changes, and track policy compliance.
Identity Management processes
- Identification establishes who you claim to be: The user claims an identity, usually by supplying a user ID or a user name.
- Authentication verifies that you are who you claim to be: The user supplies authentication information, which proves the binding between the user and the identity.
- Authorization establishes what you‘re allowed to do e.g. which files and applications you may access: The systems authorizes the (authenticated) user to do what he is allowed to do.
- Accounting or Logging for what you do.
Technical terminologies used
- Digital Identity (Digital Id) – The collection of bits of identity information about user in all the relevant IT systems at cloud service provider. The identity must be unique in a domain.
- Authentication (AuthN) – The process that allows to verify the identity of a principal, by any means, be them electronic or physical. This proof of identity is also known as credentials.
- Authorisation (AuthR) – The process that validates the user’s rights on a given resource, and, usually, enforces them. Also called as AuthS or AuthZ.
- Authentication and Authorisation Infrastructure (AAI) – A coordinated set of systems that allows institutions to collaborate in exchanging identity data to control the access to services by their respective members.
- Identity Provider (IdP) – it is also called as identity source. The company that holds all the necessary information for identifying a principal, be it a person, a system or a service.
- Service Provider (SP0 – it is also called as identity consumer. It needs to know the identity of a principal and, probably, some associated information, in order to grant access to a resource.
- System of Record (SoR) – Those systems that collect data about individuals i.e., through which individuals enter the organization. For example: student registration or Human Resources.
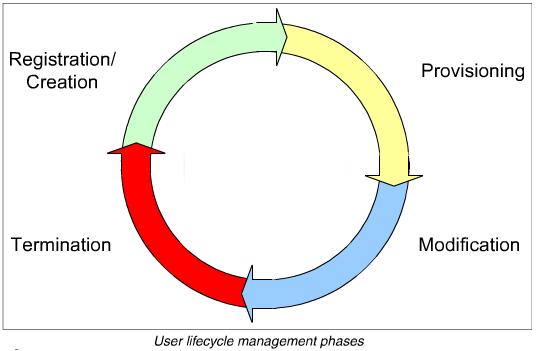
Identity Lifecycle Management
A lifecycle is a term to describe how persons or accounts for a person are created, managed, and terminated based on certain events or a time-based paradigm. The cycle represents a closed-loop process where a user is registered to use an IT asset, an account is created, and access provisioning occurs to give this user account access to system resources. Over time modifications occur where access to some resources is granted while access to other resources may be revoked. The cycle ends when the user separates from the business and the termination process removes access. It involves various phases as
- The creation cycle – It includes user creation with the identity management solution with user attributes, like user name, e-mail address, phone number, etc. It also does account creation using attributes from the user entity.
- The provisioning cycle – The provisioning cycle includes verifying the user’s identity and assigning a role. It also includes granting approval for the appropriate systems and creating the user’s identity in appropriate directories. Service Provisioning Markup Language (SPML) provides XML based structures for representing provisioning or de-provisioning requests. SPML can make use of Service Administered Markup Language (SAML) which defines an XML based framework for exchanging security information for enabling SSO (Single Sign on) or identity federation.
- The modification cycle – It is the maintenance phase of the lifecycle, administrators maintain
the various elements as
- Person – The person’s attributes, such as name, e-mail address, and phone number.
- Identity – The user’s credentials (user name, password) and information about the user
- Access rights – The level and rights of access to systems, accounts, and applications.
- Policy management – Updating access and enforcement of corporate policies.
- Privacy – Securing privacy of information that are related to specific individuals.
Users should experience changes in access rights as the organization changes and as their roles within the organization change.
- The termination cycle – This phase disables or deletes user accounts after verifying relationship between the user and the organization
Identity Management Systems
Various identity management systems used are discussed
OpenID
With OpenID a user uses one username and one password to access many web applications. The user authenticate to an OpenID server to get his/her OpenID and use the token to authenticate to web applications. A user of OpenID does not need to provide a service provider with his credentials or other sensitive information such as an email address.
OpenID is a decentralized authentication protocol with no central authority approve or register OpenID Providers. An end user can freely choose which OpenID Provider (OP or OpenID Authentication server) on which a service provider relies to assert the authenticity of identity of the consumer) to use, and can preserve their Identifier if they switch OpenID Providers.
OpenID is highly susceptible to phishing attacks, as the whole OpenID structure hinges on the URL routing to the correct machine on the Internet i.e. the OpenID Provider. A user who visits an evil site (through conventional phishing or DNS cache poisoning), sends the imposter service provider her URL. The provider consults the URL’s content to determine the location of her OP (OpenID provider). Instead of redirecting the user to the legitimate OP, it redirects her to the Evil Scooper site. The Evil Scooper contacts the legitimate OP and pulls down an exact replica of its login experience (it can even simply become a “man in the middle”). Convinced she is talking to her OP, the user posts her credentials (username and password) which can now be used by the Evil Scooper to get tokens from the legitimate OP. These tokens can then be used to gain access to any legitimate Service Provider.
PRIME (Privacy and Identity Management for Europe)
PRIME, is a single application — the PRIME Console — that handles user’s personal data. It handles management and disclosure of personal data for the user (e.g. informed consent of the user to be established and privacy risks to be conveyed, through a user interface) and is the interface to the PRIME technology.
The Console requires installation and configuration. The user manages her personal data using the console, discloses personal data, and checks the proper handling of her data by the various services she requires. The client application mirrors the server application used by the service provider.
A major challenge for a large scale adoption of PRIME technology is that it requires both individuals and service providers to implement the PRIME middleware, on both sides. Another prerequisite for large scale adoption is interoperability. PRIME, stands no chance unless it allows interoperability with existing applications and other identity management systems. This calls for standardization.

