DNS
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. Most prominently, it translates domain names, which can be easily memorized by humans, to the numerical IP addresses needed for the purpose of computer services and devices worldwide. The Domain Name System is an essential component of the functionality of most Internet services because it is the Internet’s primary directory service.
The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. Authoritative name servers are assigned to be responsible for their supported domains, and may delegate authority over sub-domains to other name servers. This mechanism provides distributed and fault tolerant service and was designed to avoid the need for a single central database.
The Domain Name System also specifies the technical functionality of the database service which is at its core. It defines the DNS protocol, a detailed specification of the data structures and data communication exchanges used in DNS, as part of the Internet Protocol Suite. Historically, other directory services preceding DNS were not scalable to large or global directories as they were originally based on text files, prominently the HOSTS.TXT resolver. DNS has been in wide use since the 1980s.
The Internet maintains two principal namespaces, the domain name hierarchy and the Internet Protocol (IP) address spaces. The Domain Name System maintains the domain name hierarchy and provides translation services between it and the address spaces. Internet name servers and a communication protocol implement the Domain Name System. A DNS name server is a server that stores the DNS records for a domain name; a DNS name server responds with answers to queries against its database.
The most common types of records stored in the DNS database are those dealing with a DNS zone’s authority (SOA), IP addresses (A and AAAA), SMTP mail exchangers (MX), name servers (NS), pointers for reverse DNS lookups (PTR), and domain name aliases (CNAME). Although not intended to be a general purpose database, DNS can store records for other types of data for either automatic machine lookups for things like DNSSEC records, or for human queries like responsible person (RP) records. As a general purpose database, DNS has also seen use in combating unsolicited email (spam) by using a real-time blackhole list stored in a DNS database. Whether for Internet naming or for general purpose uses, the DNS database is traditionally stored in a structured zone file.
DNS normally moves information from one DNS server to another through the DNS zone transfer process. If a domain contains more than one name server, only one of these servers will be the primary. Any other servers in the domain will be secondary servers. Zone transfers are much like the DHCP process in that each is a four-step process. DNS zone transfers function as
- The secondary name server starts the process by requesting the SOA record from the primary name server.
- The primary then checks the list of authorized servers, and if the secondary server’s name is on that list, the SOA record is sent.
- The secondary must then check the SOA record to see if there is a match against the SOA it already maintains. If the SOA is a match, the process stops here; however, if the SOA has a serial number that is higher, the secondary will need an update. The serial number indicates if changes were made since the last time the secondary server synchronized with the primary server. If an update is required, the secondary name server will send an All Zone Transfer (AXFR) request to the primary server.
- Upon receipt of the AXFR, the primary server will send the entire zone file to the secondary name server.
The DNS authoritative servers for website are the addresses that an attacker will target to attempt a zone transfer.
The steps to try and force a zone transfer are shown
- nslookup from the command line.
- Enter the IP address of the authoritative server for that zone.
- set type = any. It tells nslookup to query for any record.
- ls d <domain name> – Domain name is the name of the targeted domain that performs zone transfer.
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. A company may have both internal and external DNS servers that can yield information such as usernames, computer names, and IP addresses of potential target systems. NSlookup, DNSstuff, the American Registry for Internet Numbers (ARIN), and Whois can all be used to gain information that can then be used to perform DNS enumeration.
There are a lot of tools that can be used to gain information for performing DNS enumeration. The examples of tool that can be used for DNS enumeration are NSlookup, DNSstuff, American Registry for Internet Numbers (ARIN), and Whois. To enumerate DNS, you must have understanding about DNS and how it works.
The list of DNS record provides an overview of types of resource records (database records) stored in the zone files of the Domain Name System (DNS). The DNS implements a distributed, hierarchical, and redundant database for information associated with Internet domain names and addresses. In these domain servers, different record types are used for different purposes. The following list describes the common DNS record types and their use
- A (address)—Maps a host name to an IP address
- SOA (Start of Authority)—Identifies the DNS server responsible for the domain information
- CNAME (canonical name)—Provides additional names or aliases for the address record
- MX (mail exchange)—Identifies the mail server for the domain
- SRV (service)—Identifies services such as directory services
- PTR (pointer)—Maps IP addresses to host names
- NS (name server)—Identifies other name servers for the domain
Tools like DNSenum, Fierce, dig and host command are used for DNS enumeration
NSlookup
NSlookup queries DNS servers for record information. It’s included in Unix, Linux, and Windows operating systems. Hacking tools such as Sam Spade also include NSlookup tools.
Building on the information gathered from Whois, you can use NSlookup to find additional IP addresses for servers and other hosts. Using the authoritative name server information from Whois (AUTH1.NS.NYI.NET ), you can discover the IP address of the mail server.
nslookup is a network administration command-line tool available for many computer operating systems for querying the Domain Name System (DNS) to obtain domain name or IP address mapping or for any other specific DNS record.
Early in the development of BIND 9, the Internet Systems Consortium planned to deprecate nslookup in favor of host and dig. However, this decision was reversed in 2004 with the release of BIND 9.3, and nslookup has been fully supported since then.
nslookup operates in interactive or non-interactive mode. When used interactively by invoking it without arguments or when the first argument is – (minus sign) and the second argument is a hostname or Internet address of a name server, the user issues parameter configurations or requests when presented with the nslookup prompt (>). When no arguments are given, then the command queries the default server. The – (minus sign) invokes subcommands which are specified on the command line and should precede nslookup commands. In non-interactive mode, i.e. when the first argument is a name or Internet address of the host being searched, parameters and the query are specified as command line arguments in the invocation of the program. The non interactive mode searches the information for a specified host using the default name server.
Using nslookup on Windows
Nslookup.exe can be run in two modes: interactive and non-interactive. Non-interactive mode is useful when only a single piece of data needs to be returned. The syntax for non-interactive mode is:
nslookup [-option] [hostname] [server]
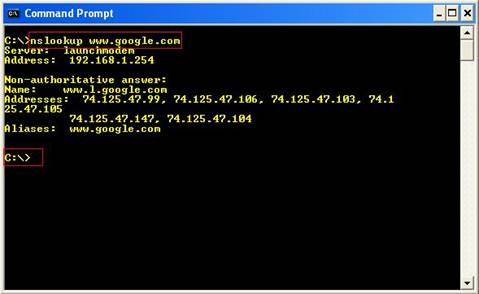
To start Nslookup.exe in interactive mode, simply type “nslookup” at the command prompt:
C:\> nslookup
Default Server: nameserver1.domain.com
Address: 10.0.0.1
>
Typing “help” or “?” at the command prompt will generate a list of available commands. Anything typed at the command prompt that is not recognized as a valid command is assumed to be a host name and an attempt is made to resolve it using the default server. To interrupt interactive commands, press CTRL+C. To exit interactive mode and return to the command prompt, type exit at the command prompt.
The following is the help output and contains the complete list of options:
Commands:(identifiers are shown in uppercase, [] means optional)
NAME- print info about the host/domain NAME using default server
NAME1 NAME2 – as above, but use NAME2 as server
help or ? – print info on common commands
set OPTION- set an option
all – print options, current server and host
[no]debug – print debugging information [no]d2 – print exhaustive debugging information [no]defname- append domain name to each query [no]recurse- ask for recursive answer to query [no]search – use domain search list [no]vc – always use a virtual circuitdomain=NAME- set default domain name to NAME
srchlist=N1[/N2/…/N6] – set domain to N1 and search list to N1, N2, and so on
root=NAME – set root server to NAME
retry=X – set number of retries to X
timeout=X – set initial time-out interval to X seconds
type=X – set query type (for example, A, ANY, CNAME, MX, NS, PTR, SOA, SRV)
querytype=X- same as type
class=X – set query class (for example, IN (Internet), ANY)
[no]msxfr – use MS fast zone transferixfrver=X – current version to use in IXFR transfer request
server NAME – set default server to NAME, using current default server
lserver NAME – set default server to NAME, using initial server
finger [USER]- finger the optional NAME at the current default host
root- set current default server to the root
ls [opt] DOMAIN [> FILE] – list addresses in DOMAIN (optional: output to FILE)
-a – list canonical names and aliases
-d – list all records
-t TYPE – list records of the given type (for example, A, CNAME, MX, NS, PTR, and so on)
view FILE – sort an ‘ls’ output file and view it with pg
exit- exit the program
A number of different options can be set in Nslookup.exe by running the set command at the command prompt. A complete listing of these options is obtained by typing set all.
Whois
WHOIS (pronounced as the phrase who is) is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block, or an autonomous system, but is also used for a wider range of other information. The protocol stores and delivers database content in a human-readable format. The WHOIS protocol is documented in RFC 3912.
WHOIS lookups were traditionally performed with a command line interface application, but now many alternative web-based tools exist. A WHOIS database consists of a set of text records for each resource. These text records consists of various items of information about the resource itself, and any associated information of assignees, registrants, administrative information, such as creation and expiration dates.
Two data models exist for storing resource information in a WHOIS database, the thick and the thin model. WHOIS information can be stored and looked up according to either a thick or a thin data model:
- Thick – A Thick WHOIS server stores the complete WHOIS information from all the registrars for the particular set of data (so that one WHOIS server can respond with WHOIS information on all .org domains, for example).
- Thin – A Thin WHOIS server stores only the name of the WHOIS server of the registrar of a domain, which in turn has the full details on the data being looked up (such as the .com WHOIS servers, which refer the WHOIS query to the registrar where the domain was registered).
With the advent of the World Wide Web and especially the loosening up of the Network Solutions monopoly, looking up WHOIS information via the web has become quite common. At present, popular web-based WHOIS-queries may be conducted from ARIN, RIPE and APNIC. Most early web-based WHOIS clients were merely front-ends to a command-line client, where the resulting output just gets displayed on a web page with little, if any, clean-up or formatting.
Currently, web based WHOIS clients usually perform the WHOIS queries directly and then format the results for display. Many such clients are proprietary, authored by domain name registrars.
The need for web-based clients came from the fact that command-line WHOIS clients largely existed only in the Unix and large computing worlds. Microsoft Windows and Macintosh computers had no WHOIS clients installed by default, so registrars had to find a way to provide access to WHOIS data for potential customers. Many end-users still rely on such clients, even though command line and graphical clients exist now for most home PC platforms. Microsoft provides the Sysinternals Suite that includes a whois client at no cost.
There are also many sites not owned by registrars or Internet-related companies. These support most of main TLD and remain free. But most of web-based whois sites are incomplete and do not support all TLD nor IP search.
Some work from a built-in WHOIS server list and some other try to retrieve the one which fits the TLD you ask for from a live Domain Information Groper query (command line clients do this query in background first).
CPAN has several Perl modules available that work with WHOIS servers. Many of them are not current and do not fully function with the current (2005) WHOIS server infrastructure. However, there is still much useful functionality to derive including looking up AS numbers and registrant contacts.
If the IP address of a web server is entered into the Whois lookup at www.arin.net, the network’s range can be determined.
ARIN Records
ARIN’s WHOIS service gives contact and registration information for IP addresses, autonomous system numbers (ASN), organizations or customers that are associated with these resources, and related Points of Contact (POC). It doesn’t include information on domain names or military networks.
Perhaps ARIN’s best-known function within the Internet community is the Whois directory service. Whois is driven by a large relational database with six classes of objects, all of which interconnect to create meaningful searchable information.

