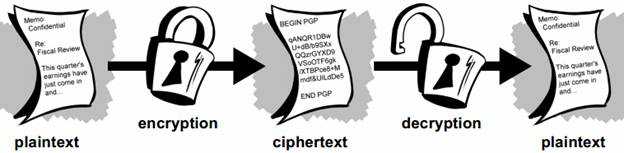
Data that can be read and understood without any special measures is called plaintext or cleartext. The method of disguising plaintext in such a way as to hide its substance is called encryption. Encrypting plaintext results in unreadable gibberish called ciphertext. You use encryption to ensure that information is hidden from anyone for whom it is not intended, even those who can see the encrypted data. The process of reverting ciphertext to its original plaintext is called decryption.
Essential Elements
There are three critical elements to data security. Confidentiality, integrity, and authentication are known as the CIA triad Data encryption provides confidentiality, message hashing provides integrity and message digital signatures provide authentication. Cryptography offers the following four basic elements
- Confidentiality – It is assurance that only authorized users can read or use confidential information.
- Authentication – It is the verification of the identity of the entities that communicate over the network.
- Integrity – It is the verification that the original contents of information have not been altered or corrupted.
- Non-repudiation – It is the assurance that a party in a communication cannot falsely deny that a part of the actual communication occurred.
Important Cryptography Terms
- Algorithm – Set of mathematical rules used in encryption and decryption.
- Cryptography – Science of secret writing that enables you to store and transmit data in a form that is available only to the intended individuals.
- Cryptosystem – Hardware or software implementation of cryptography that transforms a message to ciphertext and back to plaintext.
- Cryptanalysis – Practice of obtaining plaintext from ciphertext without a key or breaking the encryption.
- Ciphertext – Data in encrypted or unreadable format.
- Encipher – Act of transforming data into an unreadable format.
- Decipher – Act of transforming data into a readable format.
- Key – Secret sequence of bits and instructions that governs the act of encryption and decryption.
- Key clustering – Instance when two different keys generate the same ciphertext from the same plaintext.
- Keyspace – Possible values used to construct keys Plaintext Data in readable format, also referred to as cleartext.

