Cloud Computing is a modern technology which is based on internet. It uses the internet and central remote servers to maintain data and application, or you can say, it uses the computer resources that are delivered as a service over the internet. The Cloud Computing can be called as the next stage in the evolution of internet.
The salient characteristics of cloud computing based on the definitions provided by the National Institute of Standards and Terminology (NIST) are outlined below
- Cost Efficiency: Cost efficiency is the top characteristic of cloud computing model. To purchase the same amount of physical equipments and to maintain them, costs a lot that than bulk pricing from a cloud vender. IaaS is a hardware outsourcing, where users neither purchase/own the hardware, nor maintain those. User uses the hardware but its maintenance is service provider’s issue. As the traditional data centre infrastructure management is expensive due to payout for the hardware, maintenance, management and the business services that required all of this expense in the first place. The number of full-time employees (FTEs) not required for managing any hardware shows a significant savings. Since the virtual infrastructure comes with online management tools for creating new servers, installing operating systems, presenting storage and configuring network hence, fewer FTEs are needed to handle the job.
- On-demand self-service: A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service’s provider.
- Broad network access: Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, laptops, and PDAs).
- Resource pooling: The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. Examples of resources include storage, processing, memory, network bandwidth, and virtual machines.
- Device and location independence enable users to access systems using a web browser regardless of their location or what device they are using. There is a sense of location-independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or data centre).
- Rapid elasticity: Capabilities can be rapidly and elastically provisioned, in some cases automatically, to quickly scale out and rapidly released to quickly scale in. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be purchased in any quantity at any time.
- Measured service: Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be managed, controlled, and reported providing transparency for both the provider and consumer of the utilized service.
- Application programming interface (API) accessibility to software that enables machines to interact with cloud software in the same way the user interface facilitates interaction between humans and computers. Cloud computing systems typically use REST-based APIs (Representational State Transfer).
Cloud types
Cloud computing can be divided into three different models: public, hybrid, and private. While the three models have common traits, they also have different key features that make one model a better choice to meet business’ IT needs.
The Private Cloud
The Private Cloud is dedicated to private infrastructure. You can consider your personal data centre setup as a Private Cloud IaaS. But unless the cloud infrastructure (virtualization, storage, extreme redundancy, etc.) is present, it is not considered as a cloud, but the basic concept is same. Two examples of private cloud solutions are VMware vCloud and Citrix VDI. It is also called “internal cloud computing,” and is the next generation of virtualization.
The Public Cloud
The Public Cloud is dedicated completely to hosted solution. Here no hardware is owed by the user. It is the traditional model that everyone thinks of when they envision cloud computing. Vendors dynamically allocate computing resources (hard drive space, RAM, and processor power) on a per-user basis through web applications. Salesforce.com and ADP are two well-known vendors that offer public cloud computing services.
The Hybrid Cloud
The Hybrid Cloud combines the concept of both Private as well as Public. Most company evolved into this type of cloud from a traditional, private hardware infrastructure to a cloud-based one. Generally, business applications like Exchange Server 2007 or Microsoft Dynamics will interact with a vendor-hosted service. For example, Cisco, offers IronPort Email Security as their hybrid solution and Google, known for hosted solution, offers Postini email archiving.
Mixing of Private Cloud with Public Cloud is the best solution for you and your customer. It intermingle the privacy of a traditional data centre with the hosted cloud infrastructure. It can be said that, companies will transition their data recovery efforts to the Public Cloud while retaining production and operations in-house by a Private Cloud.
Cloud service models
The basic cloud service models are as follows
Infrastructure as a Service (IaaS)
Infrastructure as a Service (IaaS) is that part of cloud computing that allows leasing and managing computing infrastructure for business needs. This consists of virtual machines (VMs) run as guests by a hypervisor, like Xen or KVM with operating system, middleware, network, storage, data and applications.
The vendor also supplies a management interface in which one can interact with the Services. Payment for computing resources in done with respect to number of User’s system, time duration (generally per hour), usage of bandwidth (generally in gigabyte), storage(generally in gigabyte) or combination of any.
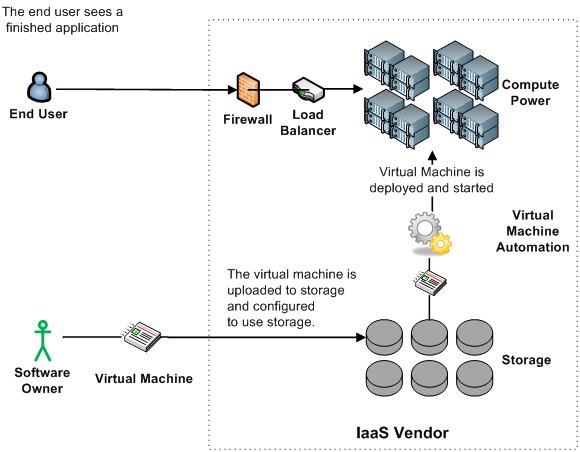
Figure 1: IaaS model
IaaS cloud providers and vendors provide the physical hardware that they own and manage in the backhand, supply on demand from large pools in data centers. Examples of IaaS include: Amazon CloudFormation (and underlying services such as Amazon EC2), Rackspace Cloud, Terremark and Google Compute Engine. User installs operating system images on the machines as well as needed application software. The end user is responsible for patching and maintaining the operating systems and application software.
Platform as a Service (PaaS)
Platform as a Service are development platforms for which the development tool itself is hosted in the cloud and accessed through a browser. With PaaS, developer can build web applications without installing any tools on their computer and then deploy those applications without any specialized systems administration skills. PaaS service providers deliver a computing platform with operating system, programming execution environment, database, and web server. The computer and storage resources scale automatically to match application demand in PaaS.
The alternative to PaaS is to develop web applications using desktop development tools like Eclipse, and then manually deploy those applications to a cloud hosting provider. PaaS requires the following elements as a minimum requirement
- Browser-based development studio – If you have to install something on your computer to develop applications.
- Seamless deployment to hosted runtime environment – Ideally, a developer should be able to deploy a PaaS application with one click.
- Management and monitoring tools – While cloud-based solutions are very cost effective, but are tricky to manage and scale without good tools. Hence, monitoring tools to monitor cloud application are needed.
- Pay as you go billing – Avoiding upfront costs has made PaaS popular as payment is based on actual usage of resources.
PaaS platforms also have functional differences from traditional development platforms. These include
- Multi-tenant development tool: traditional development tools are single user – a cloud-based studio must support multiple users, each with multiple active projects.
- Multi-tenant deployment architecture: scalability is often not a concern of the initial development effort and is left instead for the administrators to deal with when the project deploys. In PaaS, scalability of the application and data tiers must be built-in (e.g., load balancing, failover need to be basic elements of the dev platform itself).
- Integrated management: traditional development solution usually does not concern themselves with runtime monitoring, but in PaaS, the monitoring ability needs to be integrated into the development platform.
- Integrated billing: PaaS offerings require mechanisms for billing based on usage that are unique to the SaaS world.
Software as a Service
Software as a Service (SaaS), works as a software supplier. It is a software supplying model where software and data are hosted on the cloud. SaaS is accessed by users via web browser.
SaaS in the present technical industry have become a common delivery model for many business applications, including accounting, collaboration, customer relationship management (CRM), management information systems (MIS), enterprise resource planning (ERP), invoicing, human resource management (HRM), content management (CM) and service desk management. One of the biggest selling points for these companies is the potential to reduce IT support costs by outsourcing hardware and software maintenance and support to the SaaS provider.
Centralized hosting of business applications dates back to the 1960s. Starting in that decade, IBM and other mainframe providers conducted a service bureau business often referred to as time sharing or utility computing. Such services included offering computing power and database storage to banks and other large organizations from their worldwide data centers.
Cloud Security
Cloud computing security or cloud security is a part of information security. It refers to policies, technologies and controls deployed to protect data, applications, and the resources of cloud computing being used by organization.
There are a number of security issues with cloud computing faced either by cloud providers or their customers. The cloud service provider must ensure that their infrastructure is secure and clients’ data and applications are protected while the customer must ensure that the provider has taken the proper security measures to protect their information.
Threats And Security Issues
- Abuse and Nefarious Use of Cloud Computing
- Insecure Application Programming Interfaces
- Malicious Insiders
- Shared Technology Vulnerabilities
- Data Loss/Leakage
- Account, Service & Traffic Hijacking
- Unknown Risk Profile
Abuse and nefarious use of cloud computing
IaaS providers offer their customers the illusion of unlimited compute, network, and storage capacity — often coupled with a ‘frictionless’ registration process where anyone with a valid credit card can register and immediately begin using cloud services. Some providers even offer free limited trial periods. By abusing the relative anonymity behind these registration and usage models, spammers, malicious code authors, and other criminals have been able to conduct their activities with relative impunity. PaaS providers have traditionally suffered most from this kind of attacks; however, recent evidence shows that hackers have begun to target IaaS vendors as well. Future areas of concern include password and key cracking, DDOS, launching dynamic attack points, hosting malicious data, botnet command and control, building rainbow tables, and CAPTCHA solving farms.
Remediation
- Stricter initial registration and validation processes.
- Enhanced credit card fraud monitoring and coordination.
- Comprehensive introspection of customer network traffic.
- Monitoring public blacklists for one’s own network blocks.
Impact
Criminals continue to leverage new technologies to improve their reach, avoid detection, and improve the effectiveness of their activities. Cloud Computing providers are actively being targeted, partially because their relatively weak registration systems facilitate anonymity, and providers’ fraud detection capabilities are limited.
Insecure interfaces and APIs
Cloud computing providers expose a set of software interfaces or APIs that customers use to manage and interact with cloud services. Provisioning, management, orchestration, and monitoring are all performed using these interfaces. The security and availability of general cloud services is dependent upon the security of these basic APIs. From authentication and access control to encryption and activity monitoring, these interfaces must be designed to protect against both accidental and malicious attempts to circumvent policy. Furthermore, organizations and third parties often build upon these interfaces to offer value-added services to their customers. This introduces the complexity of the new layered API; it also increases risk, as organizations may be required to relinquish their credentials to third parties in order to enable their agency.
Remediation
- Analyze the security model of cloud provider interfaces.
- Ensure strong authentication and access controls are implemented in concert with encrypted transmission.
- Understand the dependency chain associated with the API.
Impact
While most providers strive to ensure security is well integrated into their service models, it is critical for consumers of those services to understand the security implications associated with the usage, management, orchestration and monitoring of cloud services. Reliance on a weak set of interfaces and APIs exposes organizations to a variety of security issues related to confidentiality, integrity, availability and accountability.
Malicious insiders
The threat of a malicious insider is well-known to most organizations. This threat is amplified for consumers of cloud services by the convergence of IT services and customers under a single management domain, combined with a general lack of transparency into provider process and procedure. For example, a provider may not reveal how it grants employees access to physical and virtual assets, how it monitors these employees, or how it analyzes and reports on policy compliance.
To complicate matters, there is often little or no visibility into the hiring standards and practices for cloud employees. This kind of situation clearly creates an attractive opportunity for an adversary — ranging from the hobbyist hacker, to organized crime, to corporate espionage, or even nation-state sponsored intrusion. The level of access granted could enable such an adversary to harvest confidential data or gain complete control over the cloud services with little or no risk of detection.
Remediation
- Enforce strict supply chain management and conduct a comprehensive supplier assessment.
- Specify human resource requirements as part of legal contracts.
- Require transparency into overall information security and management practices, as well as compliance reporting.
- Determine security breach notification processes.
Impact
The impact that malicious insiders can have on an organization is considerable, given their level of access and ability to infiltrate organizations and assets. Brand damage, financial impact, and productivity losses are just some of the ways a malicious insider can affect an operation. As organizations adopt cloud services, the human element takes on an even more profound importance. It is critical therefore those consumers of cloud services understand what providers are doing to detect and defend against the malicious insider threat.
Shared technology issues
IaaS vendors deliver their services in a scalable way by sharing infrastructure. Often, the underlying components that make up this infrastructure (e.g., CPU caches, GPUs, etc.) were not designed to offer strong isolation properties for a multi-tenant architecture. To address this gap, a virtualization hypervisor mediates access between guest operating systems and the physical compute resources. Still, even hypervisors have exhibited flaws that have enabled guest operating systems to gain inappropriate levels of control or influence on the underlying platform. A defense in depth strategy is recommended, and should include compute, storage, and network security enforcement and monitoring. Strong compartmentalization should be employed to ensure that individual customers do not impact the operations of other tenants running on the same cloud provider. Customers should not have access to any other tenant’s actual or residual data, network traffic, etc.
Remediation
- Implement security best practices for installation/configuration.
- Monitor environment for unauthorized changes/activity.
- Promote strong authentication and access control for administrative access and operations.
- Enforce service level agreements for patching and vulnerability remediation.
- Conduct vulnerability scanning and configuration audits.
Impact
Attacks have surfaced in recent years that target the shared technology inside Cloud Computing environments. Disk partitions, CPU caches, GPUs, and other shared elements were never designed for strong compartmentalization. As a result, attackers focus on how to impact the operations of other cloud customers, and how to gain unauthorized access to data.
Data loss or leakage
There are many ways to compromise data. Deletion or alteration of records without a backup of the original content is an obvious example. Unlinking a record from a larger context may render it unrecoverable, as can storage on unreliable media. Loss of an encoding key may result in effective destruction. Finally, unauthorized parties must be prevented from gaining access to sensitive data.
The threat of data compromise increases in the cloud, due to the number of and interactions between risks and challenges which are either unique to cloud, or more dangerous because of the architectural or operational characteristics of the cloud environment.
Remediation
- Implement strong API access control.
- Encrypt and protect integrity of data in transit.
- Analyzes data protection at both design and run time.
- Implement strong key generation, storage and management, and destruction practices.
- Contractually demand providers wipe persistent media before it is released into the pool.
- Contractually specify provider backup and retention strategies.
Impact
Data loss or leakage can have a devastating impact on a business. Beyond the damage to one’s brand and reputation, a loss could significantly impact employee, partner, and customer morale and trust. Loss of core intellectual property could have competitive and financial implications. Worse still, depending upon the data that is lost or leaked, there might be compliance violations and legal ramifications.
Account or service hijacking
Account or service hijacking is not new. Attack methods such as phishing, fraud, and exploitation
of software vulnerabilities still achieve results. Credentials and passwords are often reused, which amplifies the impact of such attacks.
Cloud solutions add a new threat to the landscape. If an attacker gains access to your credentials, they can eavesdrop on your activities and transactions, manipulate data, return falsified information, and redirect your clients to illegitimate sites. Your account or service instances may become a new base for the attacker. From here, they may leverage the power of your reputation to launch subsequent attacks.
Remediation
- Prohibit the sharing of account credentials between users and services.
- Leverage strong two-factor authentication techniques where possible.
- Employ proactive monitoring to detect unauthorized activity.
- Understand cloud provider security policies and SLAs.
Impact
Account and service hijacking, usually with stolen credentials, remains a top threat. With stolen credentials, attackers can often access critical areas of deployed cloud computing services, allowing them to compromise the confidentiality, integrity and availability of those services. Organizations should be aware of these techniques as well as common defense in depth protection strategies to contain the damage (and possible litigation) resulting from a breach.
Unknown risk profile
One of the tenets of Cloud Computing is the reduction of hardware and software ownership and maintenance to allow companies to focus on their core business strengths. This has clear financial and operational benefits, which must be weighed carefully against the contradictory security concerns — complicated by the fact that cloud deployments are driven by anticipated benefits, by groups who may lose track of the security ramifications.
Versions of software, code updates, security practices, vulnerability profiles, intrusion attempts, and security design, are all important factors for estimating your company’s security posture. Information about who is sharing your infrastructure may be pertinent, in addition to network intrusion logs, redirection attempts and/or successes, and other logs.
Security by obscurity may be low effort, but it can result in unknown exposures. It may also impair the in-depth analysis required highly controlled or regulated operational areas.
Remediation
- Disclosure of applicable logs and data.
- Partial/full disclosure of infrastructure details (e.g., patch levels, firewalls, etc.).
- Monitoring and alerting on necessary information.
Impact
When adopting a cloud service, the features and functionality may be well advertised, but what about details or compliance of the internal security procedures, configuration hardening, patching, auditing, and logging? How are your data and related logs stored and who has access to them? What information if any will the vendor disclose in the event of a security incident? Often such questions are not clearly answered or are overlooked, leaving customers with an unknown risk profile that may include serious threats.

